Metasploit Pivoting || Port Forwarding || Token Stealing and Impersonation

Metasploit Framework and StructureПодробнее

Pivoting, port forwarding, token stealing and impersonation (introduction) (Part 16)Подробнее

Protecting Your API from App Impersonation: Token Hijacking Guide and Mitigation of JWT TheftПодробнее

PortScanning | Pivoting | With Metasploit | Post ExploitationПодробнее

Pivoting with Metasploit IПодробнее

Pivoting with MetasploitПодробнее

Basic metasploit commandПодробнее

Pivoting, port forwarding, token stealing and impersonation (overview) (Part 22)Подробнее

Basic Pivoting Techniques: Metasploit Local Port Forwarding (through existing meterpreter session)Подробнее

Understanding token stealing and impersonation (Part 18)Подробнее

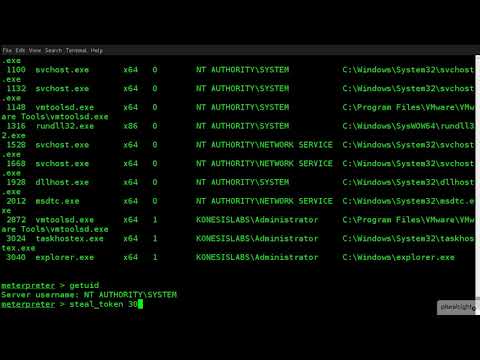
Use steal token and Incognito to impersonate accounts (Part 21)Подробнее
Pivoting | Теория | Что такое Pivoting (092)Подробнее

Tunneling Through Protected Networks | Master Network PivotingПодробнее
Pivoting attack trafficПодробнее

Pivoting In Metasploit - Metasploit Minute [Cyber Security Education]Подробнее
![Pivoting In Metasploit - Metasploit Minute [Cyber Security Education]](https://img.youtube.com/vi/MeSql-3aOsM/0.jpg)
Meterpreter Pivoting and Port Forwarding with MetasploitПодробнее

Understanding pivoting and port forwarding (Part 17)Подробнее

Metasploit 13 Post Exploitation Pivoting and Port ForwardingПодробнее
