Understanding Kubernetes Networking. Part 6: Calico Network Policies
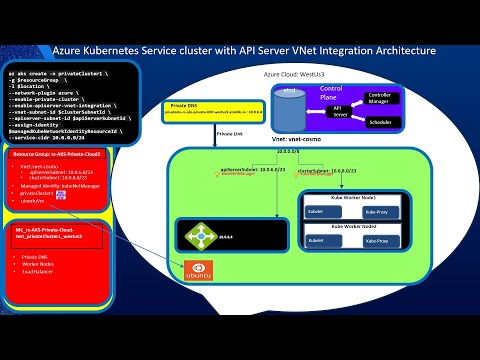
Setup Azure Kubernetes Private Clusters with API Server Vnet IntegrationПодробнее
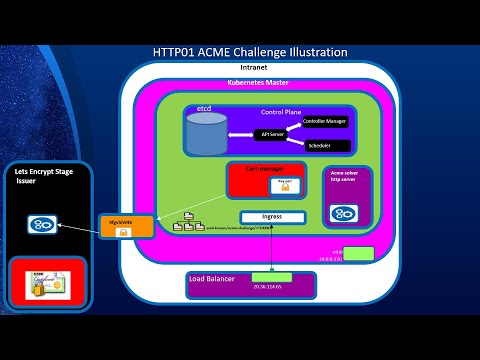
Encrypt Client Communication to Kubernetes Services Leveraging Cert-Manage and Let’s EncryptПодробнее
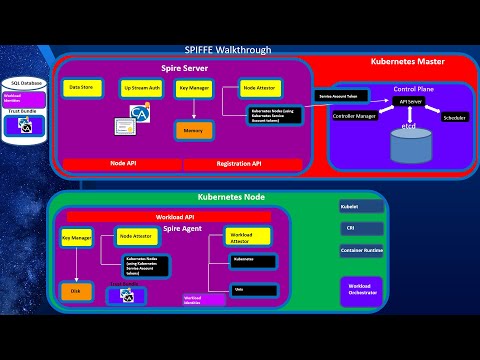
Workload Identity Part 1: Introduction to SPIFFE and SPIREПодробнее
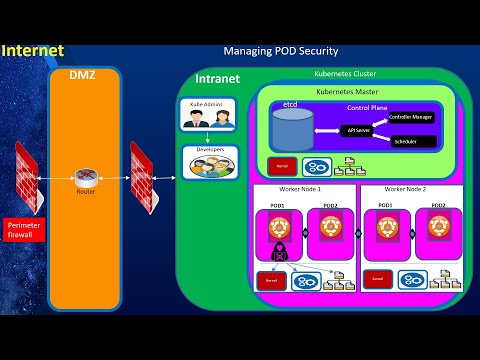
Kubernetes Security, Part 2: Managing POD Run Time SecurityПодробнее
Cilium Kubernetes CNI Provider: Part 4, IP Routing Modes (Direct and Encapsulated)Подробнее

Kubernetes Security, Part 1: Kubernetes Security Overview and Role Based Access Control (RBAC)Подробнее
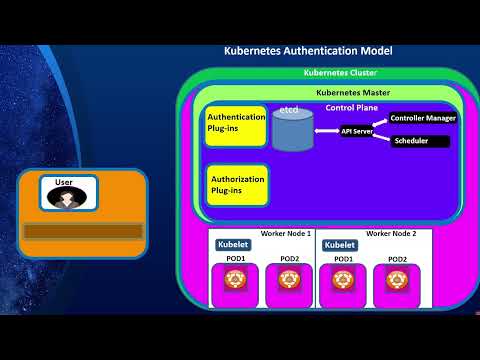
Istio Ambient Service MeshПодробнее
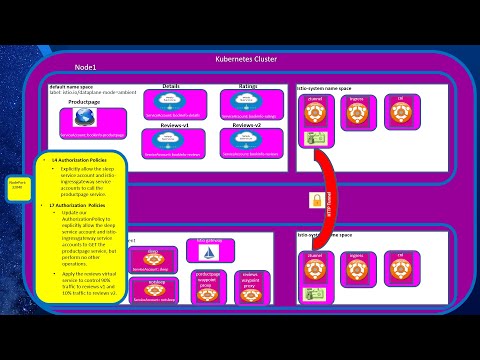
Kubernetes Security, Part 4: Kubernetes Authentication (Part B: Open ID Connect Auth)Подробнее
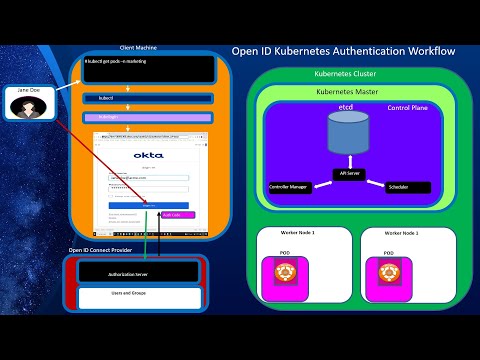
Workload Identity Part 2: How Cilium Implements Its Mutual Auth Leveraging SPIFFE and SPIREПодробнее
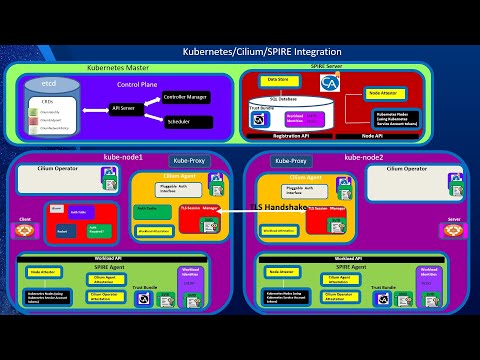
Kubernetes Security, Part 3: Kubernetes Auth (Part A: Overview and X509 Client Certificate auth)Подробнее
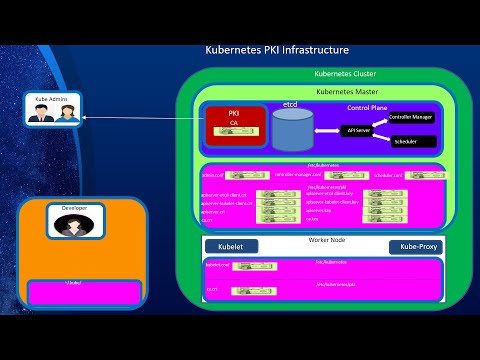
What is VXLAN and How It is Used as an Overlay Network in Kubernetes?Подробнее
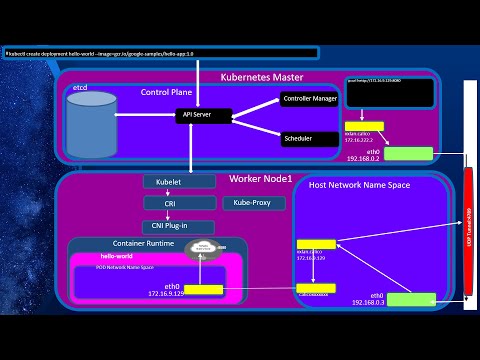
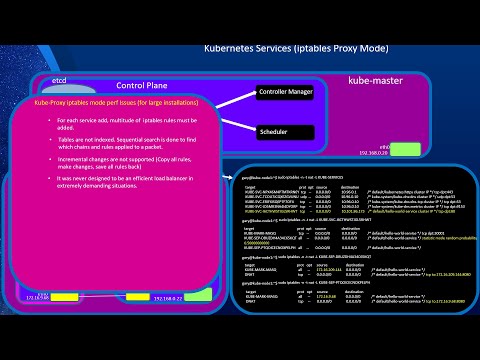
Kubernetes kube-proxy Modes: iptables and ipvs, Deep DiveПодробнее
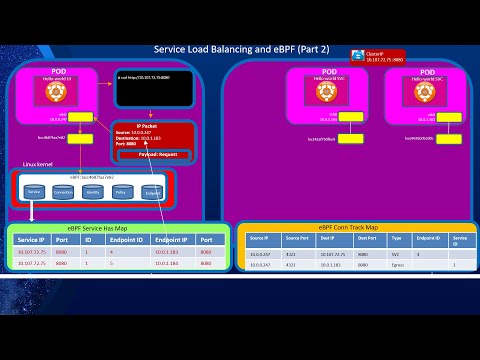
Cilium Kubernetes CNI Provider, Part 1: Overview of eBPF and Cilium and the Installation ProcessПодробнее
Kubernetes: Configuration as Data: Environment Variables, ConfigMaps, and SecretsПодробнее

Cilium Kubernetes CNI Provider, Part 3: Cluster MeshПодробнее

Configuring and Managing Storage (volumes) in KubernetesПодробнее
Managing Linux Logins, Users, and Machines in AD: Part 2- Join Linux Machines to ADПодробнее

Cilium Kubernetes CNI Provider, Part 2: Security Policies and Observability Leveraging HubbleПодробнее
Managing Linux Logins, Users, and Machines in AD: Part 1- Setup ADПодробнее

Sharing Resources between Windows and LinuxПодробнее
