USENIX Security '18 - BlackIoT: IoT Botnet of High Wattage Devices Can Disrupt the Power Grid
CS6263: With High Power Comes High ResponsibilityПодробнее

USENIX Security '19 - Not Everything is Dark and Gloomy: Power Grid Protections Against IoTПодробнее

Not-so-Smart Home: How a botnet of high wattage IoT devices can be used to attack the power gridПодробнее

Paper presentaion blackiot cwang720Подробнее

USENIX Security '22 - MaDIoT 2.0: Modern High-Wattage IoT Botnet Attacks and DefensesПодробнее
USENIX Security '18 - Rampart: Protecting Web Applications from CPU-Exhaustion Denial-of-Service...Подробнее

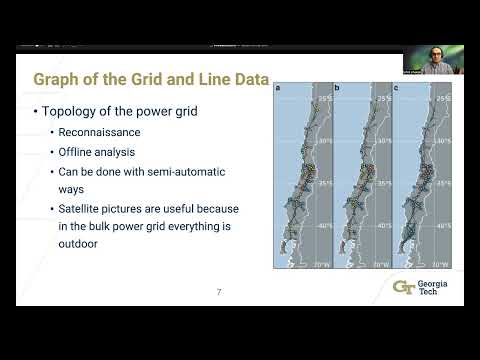
USENIX Security '18 - BlackIoT: IoT Botnet of High Wattage Devices Can Disrupt the Power GridПодробнее

USENIX Security '18 - Acquisitional Rule-based Engine for Discovering Internet-of-Things DevicesПодробнее

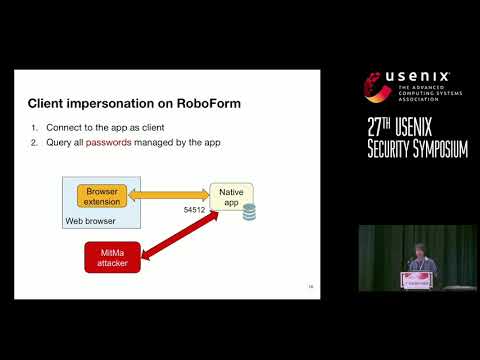
USENIX Security '18 - Man-in-the-Machine: Exploiting Ill-Secured Communication Inside the ComputerПодробнее
USENIX Security '24 - SmartCookie: Blocking Large-Scale SYN Floods with a Split-Proxy Defense...Подробнее

USENIX Security '18 - The Battle for New York: A Case Study of Applied Digital Threat Modeling...Подробнее

IoT Skimmer: Energy Market Manipulation through High-Wattage IoT BotnetsПодробнее

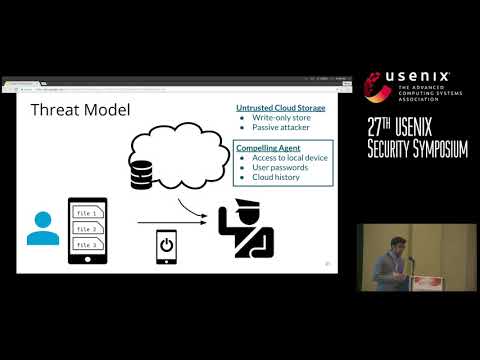
USENIX Security '18 - BurnBox: Self-Revocable Encryption in a World Of Compelled AccessПодробнее
USENIX Security '23 - HorusEye: A Realtime IoT Malicious Traffic Detection Framework using...Подробнее

USENIX Security '18 - Who Is Answering My Queries: Understanding and Characterizing Interception...Подробнее

USENIX Security '24 - MultiFuzz: A Multi-Stream Fuzzer For Testing Monolithic FirmwareПодробнее
