USENIX Security '23 - Trojan Source: Invisible Vulnerabilities
USENIX Security '23 - Trojan Source: Invisible VulnerabilitiesПодробнее

USENIX Security '23 - GLeeFuzz: Fuzzing WebGL Through Error Message Guided MutationПодробнее

USENIX Security '23 - V1SCAN: Discovering 1-day Vulnerabilities in Reused C/C++ Open-source...Подробнее

USENIX Security '23 - Sparsity Brings Vulnerabilities: Exploring New Metrics in Backdoor AttacksПодробнее

USENIX Security '23 - Medusa Attack: Exploring Security Hazards of In-App QR Code ScanningПодробнее

USENIX Security '23 - AlphaEXP: An Expert System for Identifying Security-Sensitive Kernel ObjectsПодробнее

USENIX Security '23 - Proxy Hunting: Understanding and Characterizing Proxy-based Upgradeable...Подробнее

USENIX Security '23 - Jinn: Hijacking Safe Programs with TrojansПодробнее

USENIX Security '23 - WHIP: Improving Static Vulnerability Detection in Web Application by...Подробнее

USENIX Security '23 - CipherH: Automated Detection of Ciphertext Side-channel Vulnerabilities in...Подробнее

USENIX Security '23 - Cipherfix: Mitigating Ciphertext Side-Channel Attacks in SoftwareПодробнее

USENIX Security '23 - VulChecker: Graph-based Vulnerability Localization in Source CodeПодробнее

LangSec Keynote: Trojan Source and Bad Characters: Invisible Hacks and Reluctant PatchingПодробнее

USENIX Security '22 - Web Cache Deception Escalates!Подробнее
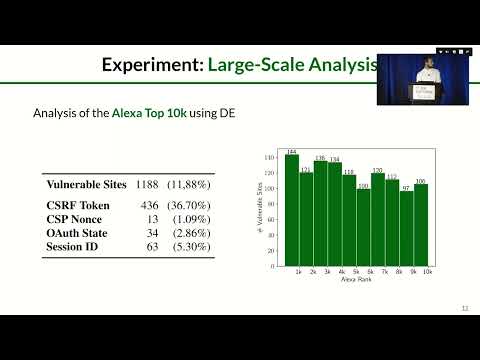
USENIX Security '23 - Hiding in Plain Sight: An Empirical Study of Web Application Abuse in MalwareПодробнее

USENIX Security '22 - FuzzOrigin: Detecting UXSS vulnerabilities in Browsers through Origin FuzzingПодробнее

USENIX Security '23 - Lost in Conversion: Exploit Data Structure Conversion with Attribute Loss...Подробнее

USENIX Security '17 - Hacking in Darkness: Return-oriented Programming against Secure EnclavesПодробнее
USENIX Security '21 - You Autocomplete Me: Poisoning Vulnerabilities in Neural Code CompletionПодробнее
