USENIX Security '21 - T-Miner: A Generative Approach to Defend Against Trojan Attacks on DNN-based
USENIX Security '21 - T-Miner: A Generative Approach to Defend Against Trojan Attacks on DNN-basedПодробнее

USENIX Security '21 - Dompteur: Taming Audio Adversarial ExamplesПодробнее

USENIX Security '21 - Explanation-Guided Backdoor Poisoning Attacks Against Malware ClassifiersПодробнее

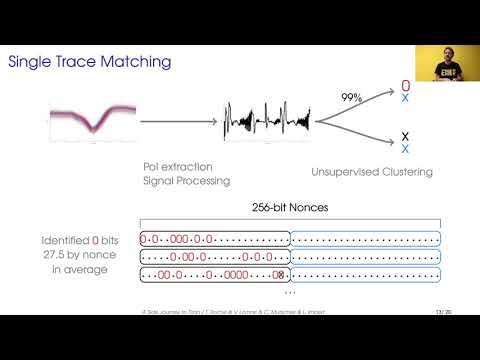
USENIX Security '21 - A Side Journey To TitanПодробнее
USENIX Security '21 - Raccoon Attack: Finding and Exploiting Most-Significant-Bit-Oracles...Подробнее

USENIX Security '23 - Trojan Source: Invisible VulnerabilitiesПодробнее

USENIX Security '21 - Jaqen: A High-Performance Switch-Native Approach for Detecting and MitigatingПодробнее

USENIX Security '21 - Defeating DNN-Based Traffic Analysis Systems in Real-Time With BlindПодробнее

USENIX Security '23 - NeuroPots: Realtime Proactive Defense against Bit-Flip Attacks in Neural...Подробнее

USENIX Security '21 - Phishpedia: A Hybrid Deep Learning Based Approach to Visually IdentifyПодробнее

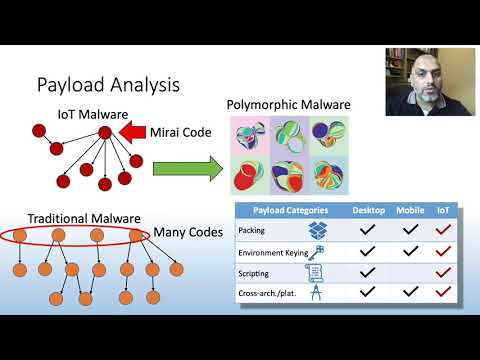
USENIX Security '21 - The Circle Of Life: A Large-Scale Study of The IoT Malware LifecycleПодробнее
USENIX Security '20 - CopyCat: Controlled Instruction-Level Attacks on EnclavesПодробнее

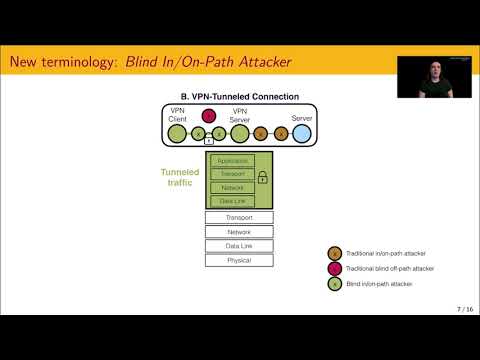
USENIX Security '21 - Blind In/On-Path Attacks and Applications to VPNsПодробнее
USENIX Security '21 - Ripple: A Programmable, Decentralized Link-Flooding Defense Against AdaptiveПодробнее

USENIX Security '24 - Practical Data-Only Attack GenerationПодробнее

USENIX Security '23 - FreeEagle: Detecting Complex Neural Trojans in Data-Free CasesПодробнее

USENIX Security '23 - TRIDENT: Towards Detecting and Mitigating Web-based Social Engineering AttacksПодробнее

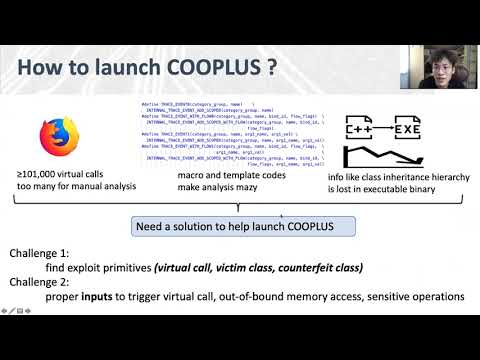
USENIX Security '21 - VScape: Assessing and Escaping Virtual Call ProtectionsПодробнее
USENIX Security '23 - Jinn: Hijacking Safe Programs with TrojansПодробнее
